Record fine for Pegasus creators. WhatsApp opened the gate to phone surveillance

- WhatsApp has won a historic lawsuit against NSO Group, obtaining $168 million in damages for unlawful spying on users via Pegasus software.
- Pegasus enabled secret data acquisition from phones, including activating the microphone and camera without the user's knowledge; it was used, among others, by Polish services. The Sejm's investigative committee is to determine whether the software was purchased legally.
- The trial revealed the secrets behind NSO’s actions, including the development of exploits, networks that masked customer data and how WhatsApp infected devices without users’ knowledge; the company operated without consent and broke US law.
- Our case will go down in history as the first victory in the fight against illegal spyware that threatens security and privacy, Meta announced Tuesday. A five-year trial against Israeli company NSO Group ended.
Jurors ruled that the company must pay the giant more than $167 million in damages for hacking into the WhatsApp messaging app using Pegasus software. The company also won an additional $400,000 in damages for the time its employees spent investigating Pegasus.
WhatsApp opened the gateway to phone surveillanceWhat is it about? WhatsApp, a Meta subsidiary, has accused NSO Group of using its Pegasus spyware program as a gateway to the phones of about 1,400 people, including dissidents, human rights activists and journalists, allowing government agencies that license the software to spy on them.
Pegasus is a very invasive tool - it allows you to collect data from all installed applications, including financial information, location, emails and text messages . What's more, the program can remotely activate the device's microphone and camera.
In investigating the traces of NSO Group's activity, WhatsApp cooperated with the Citizen Lab organization. It confirmed five cases of Pegasus use in Poland: against Krzysztof Brejza, Roman Giertych, Ewa Wrzosek, Michał Kołodziejczak and Tomasz Szwejgiert . According to information disclosed by the Minister of Justice Adam Bodnar, there were 578 people who were subjected to surveillance using this software or similar software of this class in the years 2017-2022.
The purchase of Pegasus for the Central Anticorruption Bureau was kept secret, the money for this purpose came from the Justice Fund. An investigation is underway to see whether the purchase of the software was legal, and also whether it was legal to use it against specific individuals (in Poland, consent for operational control must be issued by a court). The Sejm's investigative committee is dealing with this.
R&D searched for vulnerabilities in WhatsApp messengerThe most interesting thing about the American court case is not the verdict itself, but the unofficial transcripts of interviews with key NSO Group employees, released by Meta. "This is the first time investigators have had such broad access to information about NSO's activities - from creating exploits, through operational operations, to financial matters," summed up John Scott Railton from Citizen Lab.
The testimony focuses on how Pegasus was installed and its covert data collection feature.
According to witness statements, NSO used exploits, or software vulnerabilities, in WhatsApp. They allowed certain actions to be performed in a way that the app's creators had not anticipated. They were used so that the target of the attack did not have to click on links or open attachments for their phone to be infected.
NSO Group had an R&D department that worked on fast-tracking installation vector updates to respond to WhatsApp software updates. This usually took two to three days. The same department was also responsible for finding new security holes in the app. The Israeli company was also responsible for creating data transmission networks for customers so that they remained anonymous.

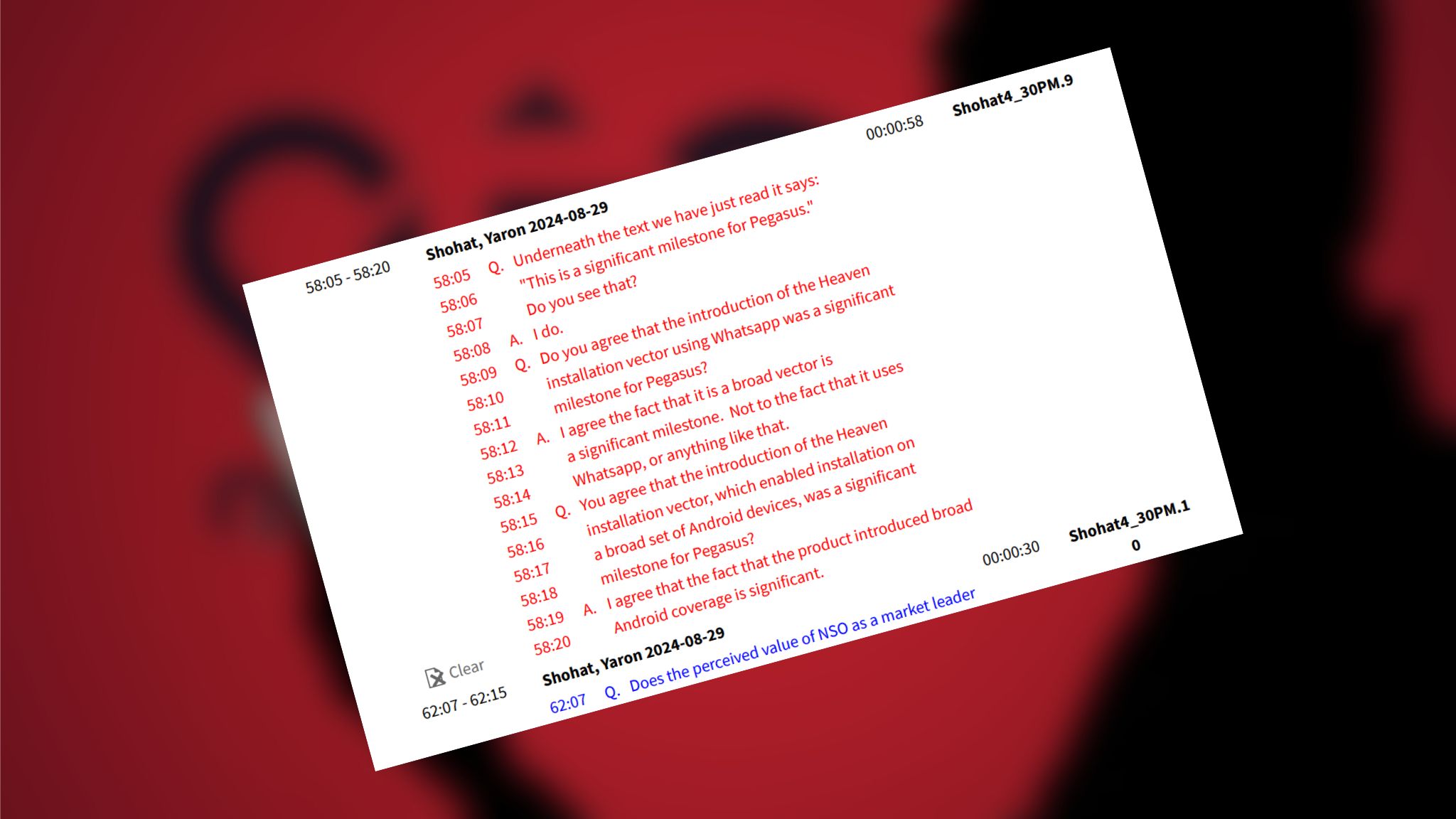
NSO has taken an interesting line of defense. Yaron Shotat, the company's CEO, when asked if they had ever tried to get permission from the company to use WhatsApp, replied that they had not, because sending a message via the messenger also does not require permission from its owner.
At the same time , during the hearing, he admitted that the ability to infect devices via WhatsApp was a market advantage for NSO Group – thanks to this, the company gained potential access to all phones with the Android operating system. It did not have to break through the manufacturers' security.
The NSO Group case itself ended in December 2024. Judge Phyllis Hamilton ruled that the company had violated federal and state law and WhatsApp’s terms of service, which prohibit the use of the app. A jury was deciding on the amount of the penalty. NSO Group spokesman Gil Lainerz said he would appeal.
In a press release Tuesday, Meta said it plans to make a donation to digital rights groups working to protect people from spyware. The company also said its next step will be to seek a court order to prevent NSO from attacking WhatsApp again.
wnp.pl





